I’ve noticed that a lot of people seem to get confused with what exactly dot1q is doing most of the time. It’s actually incredibly simply.
Tagging traffic, or Trunking in Cisco-talk, is a very straightforward process. I will not be discussing ISL here as not only do I not use it, but Cisco is phasing it out on their stuff anyway.
The dot1q tag is simply inserted into the layer2 header when a packet leaves a switchport over a trunk. If a frame leaves a switchport that is not a trunk, there is no dot1a tag inserted into it, regardless of what vlan the frame came from or is going to. This means that the following is a perfectly valid topology:
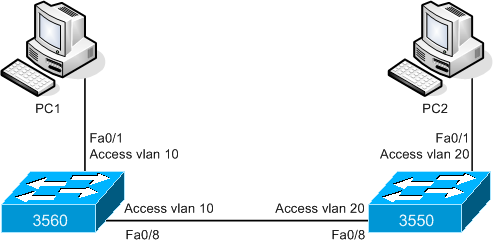
Let’s configure the above quickly.
3560TOP#conf t
Enter configuration commands, one per line. End with CNTL/Z.
3560TOP(config)#int range fa0/1, fa0/8
3560TOP(config-if-range)#switchport mode access
3560TOP(config-if-range)#switchport access vlan 10
% Access VLAN does not exist. Creating vlan 10
C3550#conf t
Enter configuration commands, one per line. End with CNTL/Z.
C3550(config)#int range fa0/1, fa0/8
C3550(config-if-range)#switchport mode access
C3550(config-if-range)#switchport access vlan 20
% Access VLAN does not exist. Creating vlan 20
Can the PC’s ping each other?
PC2#ping 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/10/28 ms
PC1#ping 10.1.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/8 ms
They both can ping each other. But aren’t the devices in different vlans? They sure are, yet they can still communicate. Why is this?
The issue is that the switch interlink are both access ports. An access port will not send or accept tagged traffic. Hence when SW1 sends PC1′s traffic over the link, the tag is removed. When that packet comes into SW2′s fa0/8 interface, that interface is part of vlan 20. SW2 will allow that frame to flow to PC2. The same happens vice-versa.
Let’s change the topology so that there is a trunk instead between the 2 switches. I also want to force the use of dot1q.
C3550#conf t
Enter configuration commands, one per line. End with CNTL/Z.
C3550(config)#default interface fa0/8
Interface FastEthernet0/8 set to default configuration
3560TOP#conf t
Enter configuration commands, one per line. End with CNTL/Z.
3560TOP(config)#default interface fa0/8
Interface FastEthernet0/8 set to default configuration
3560TOP(config-if)#switchport trunk encapsulation dot1q
Now can the PC’s ping each other?
PC2#ping 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
They cannot. It now works as expected SW1 now sends PC1′s frame over the link with a dot1q tag. In that tag is the vlan id of 10. When it gets to SW2, it’ll look at that tag and ensure the frame is not sent out any access port that is not in vlan 10.
Another important part of dot1q is the notion of a native vlan. The native vlan does not get tagged over a trunk unless you configure otherwise. Vlan1 is the default native vlan.
So let’s try something here. Let’s configure SW1 to think that vlan 10 is the native vlan, while on SW2 let’s change it to vlan20. Will my PC’s be able to ping each other?
3560TOP(config)#int fa0/8
3560TOP(config-if)#switchport trunk native vlan 10
*Mar 1 00:13:42.385: %SPANTREE-2-RECV_PVID_ERR: Received BPDU with inconsistent peer vlan id 1 on FastEthernet0/8 VLAN10.
*Mar 1 00:13:42.385: %SPANTREE-2-BLOCK_PVID_PEER: Blocking FastEthernet0/8 on VLAN0001. Inconsistent peer vlan.
*Mar 1 00:13:42.385: %SPANTREE-2-BLOCK_PVID_LOCAL: Blocking FastEthernet0/8 on VLAN0010. Inconsistent local vlan.
*Mar 1 00:14:13.389: %SPANTREE-2-UNBLOCK_CONSIST_PORT: Unblocking FastEthernet0/8 on VLAN0001. Port consistency restored.
*Mar 1 00:14:19.270: %CDP-4-NATIVE_VLAN_MISMATCH: Native VLAN mismatch discovered on FastEthernet0/8 (10), with C3550 FastEthernet0/8 (20).
I’ve done the same on SW2, but for vlan 20. You can see that the switch is giving me all kinds of error messages.
However I cannot ping between my PCs:
PC2#ping 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
I tried disabling CDP, hard coding the trunk between the 2 switches and also disabling negotiation between the 2 links but no communication at all. Even though it should work theoretically, the switches just do not like the native vlan not matching on either side of the link
I was not happy with the outcome above, so I dug a little deeper. It seems STP is blocking communication. The BPDU’s still carry vlan information with them. What I’ve done on both switches is disable STP on vlans 10 and 20 on both switches:
3560TOP(config)#no spanning-tree vlan 10,20
Can I now ping?
PC2#ping 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/8 ms
Indeed I can. So even though there is a trunk between the 2 switches and both devices are in separate vlans, they can still communicate as SW1 and SW2 both think that the native vlan matches on each side. They have no idea that PC1 is in vlan 10 and PC2 is in vlan 20.
I don’t much like leaving the native vlan untagged. Thankfully we have an option to tag all frames:
3560TOP(config)#vlan dot1q tag native
C3550(config)#vlan dot1q tag native
What this does is essentially ignore the native vlan setting. All traffic, regardless of vlan, will be tagged over the link. This is proven by the fact I can now no longer ping again:
PC2#ping 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
It’s important to note that an untagged frame is identical to a frame that goes in and out of an access port. There is no difference. To prove this I’m going to put both PC1 and PC2 into vlan 10, and them create a trunk link to PC1. PC1 does not understand trunk links and will continue to send regular traffic. I’ll configure SW1 to untag the native vlan again and make vlan 10 the native vlan. Will this work?
3560TOP(config)#int fa0/8
3560TOP(config-if)#no switchport trunk native vlan 10
3560TOP(config-if)#exit
3560TOP(config)#no vlan dot1q tag native
3560TOP(config)#int fa0/1
3560TOP(config-if)#switchport trunk encap dot
3560TOP(config-if)#switch mode trunk
3560TOP(config-if)#switchport trunk native vlan 10
Can PC1 ping PC2?
PC1#ping 10.1.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/6/16 ms
It sure can. PC1 is simply sending untagged traffic off to SW1. SW1 assumes that untagged traffic is part of vlan10 and forwards those frames throughout vlan 10. This goes over the trunk to SW2, and sends those frames over the vlan10 access ports where it gets to PC2.
Of course routers and some servers can also send tagged traffic. Let’s change PC1 so that it sends out tagged traffic. Let’s change SW1 back to the regular native vlan on port fa0/1
3560TOP(config)#int fa0/1
3560TOP(config-if)#no switchport trunk native vlan 10
PC1(config)#int fa0/0
PC1(config-if)#no ip address
PC1(config-if)#int fa0/0.1
PC1(config-subif)#encapsulation dot1Q 10
PC1(config-subif)#ip address 10.1.1.1 255.255.255.0
Can I ping?
PC1#ping 10.1.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/4/8 ms
As expected I sure can.
Just like the switches, I can also make any single vlan I choose to be the native vlan. This frame will simply be sent untagged. Let’s change SW1′s fa0/1 interface to an access port again, and change PC1 to continue to use dot1q, but ensure that vlan 10 traffic is untagged:
3560TOP(config)#default interface fa0/1
Interface FastEthernet0/1 set to default configuration
3560TOP(config)#int fa0/1
3560TOP(config-if)#switch mode access
3560TOP(config-if)#switch access vlan 10
PC1(config)#int fa0/0.1
PC1(config-subif)#encapsulation dot1Q 10 native
Ping should still work, does it?
PC1#ping 10.1.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/8 ms
As you can see, it’s pretty simple stuff at the end of the day.
Originally publish with link https://mellowd.co.uk/ccie/?p=1551